Sovereign and secure data exchange
The International Data Spaces enable open data marketplaces for the economy and serves as a blueprint for secure data ecosystems.
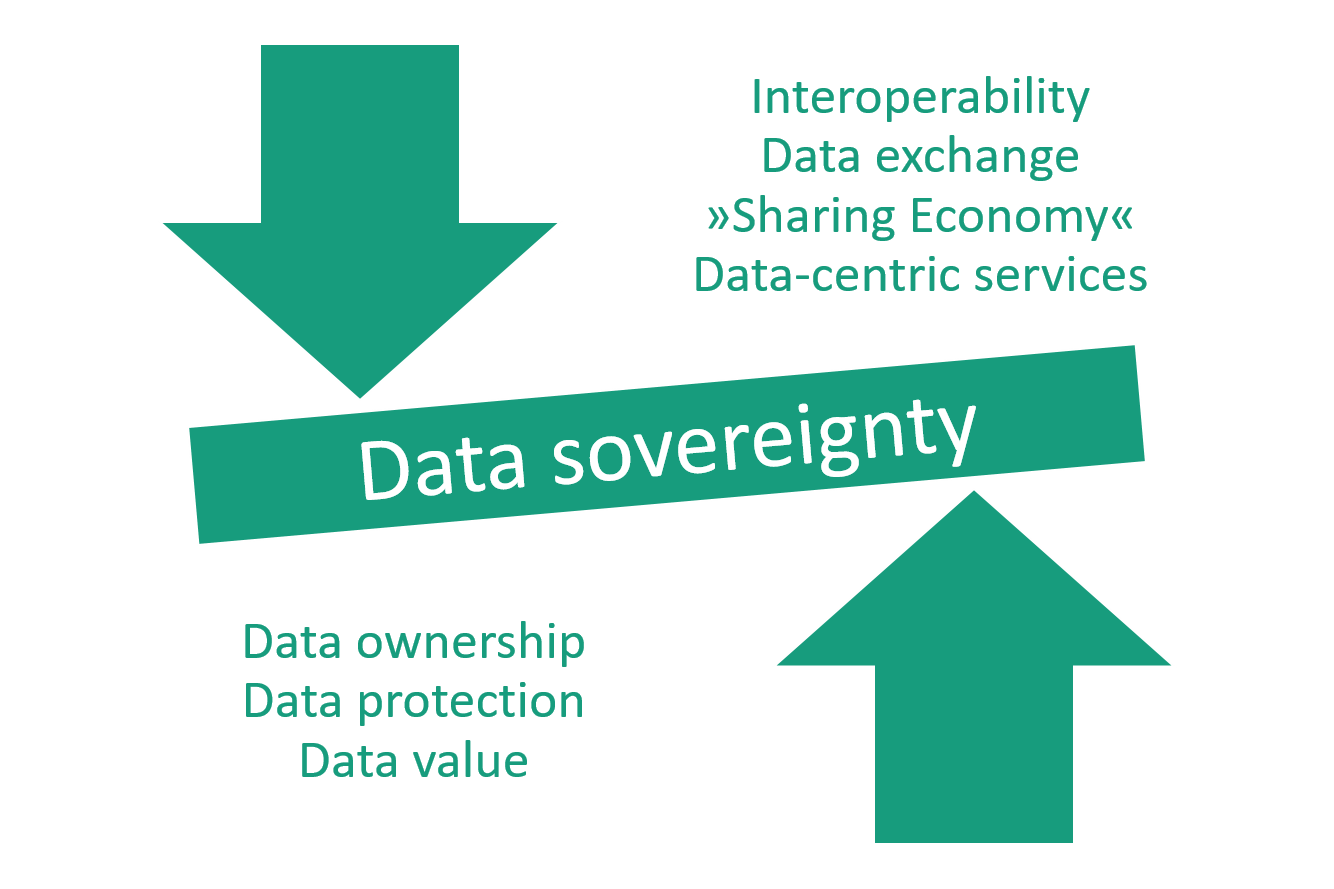
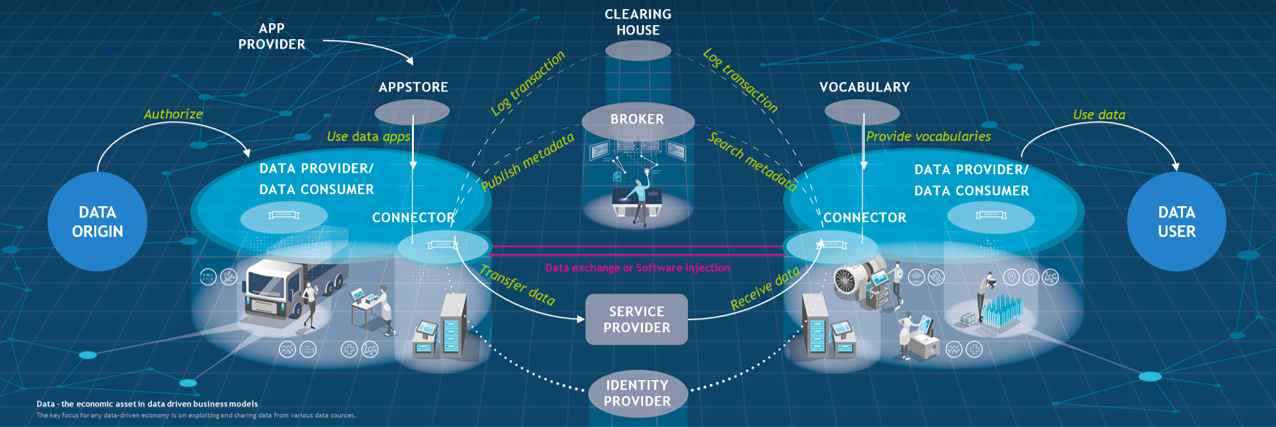
The architecture developed by the Fraunhofer-Gesellschaft establishes a framework allowing companies that provide data to exchange them with other companies while always maintaining control over the dissemination and use of these data. Thus, it establishes the basic conditions for genuine data sovereignty in the industrial context and serves as a key element of a data infrastructure in and for Europe. Telekom is already using the International Data Spaces reference architecture as an innovative platform (DIH) for the secure and efficient exchange of data. In data processing and analysis, it focuses on innovative data-driven services and applications related to machine learning and artificial intelligence (AI).
 International Data Spaces
International Data Spaces